Table of contents
Introduction
MIT released their puzzles again for HackMIT this year. Similar to prior year, the top 50 get guaranteed admission to the hackathon.
Accessing Puzzles
This year, the hint to the puzzle was Look at all the stars!. After scrolling a bit, I noticed that the constellations at the bottom of the screen would spin while scrolling. After screwing around with the infinite scroll on my mouse, I got the link to access the puzzle.

Curseword (500 points)
Curseword was a simple crossword. I got the answers through GPT and Googling.
I don’t have a screenshot of the empty puzzle, but I do have my key.
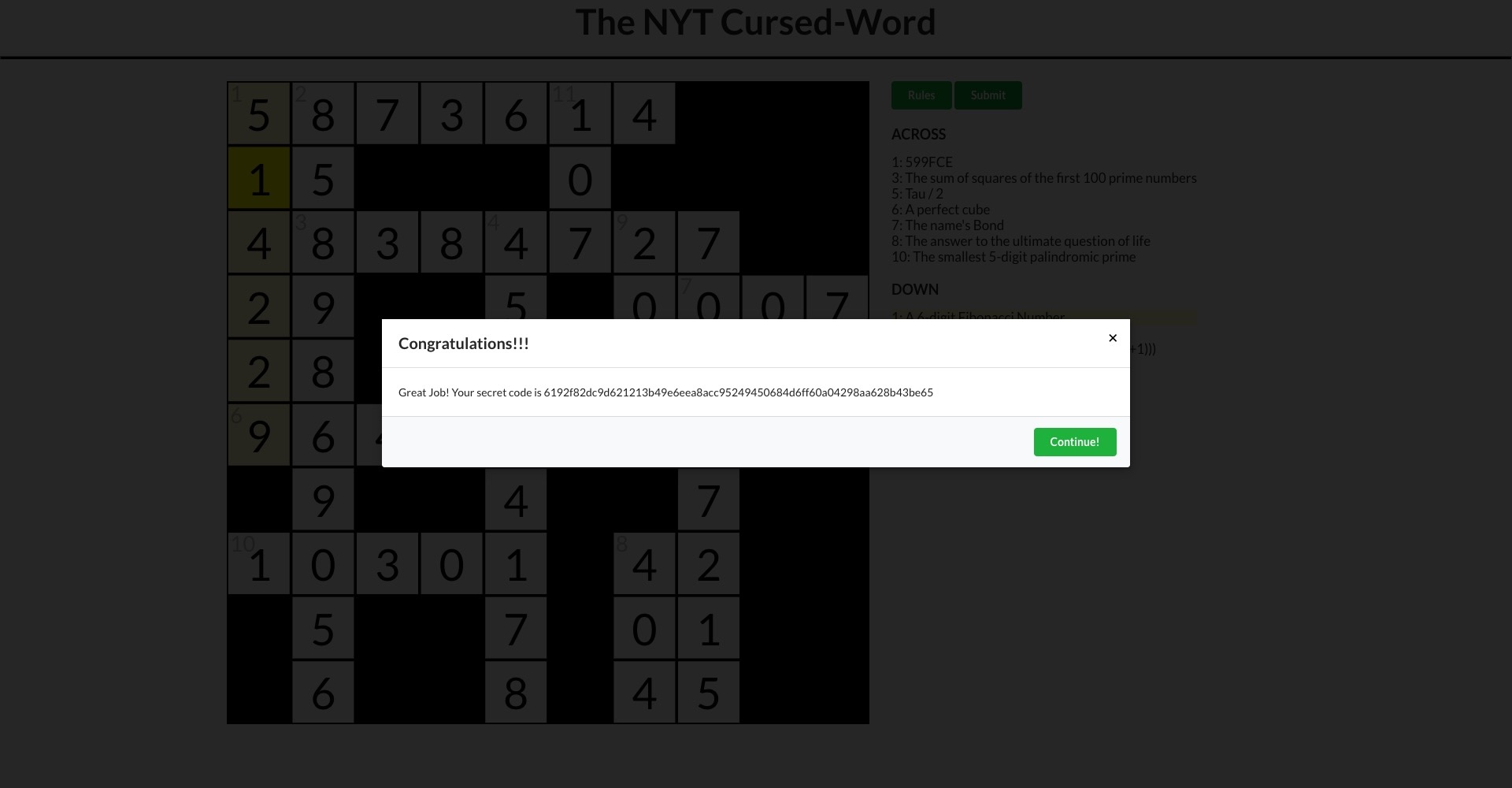
Completed July 8, 2024.
Connections (2000 points)
I decided to do Connections next as it seemed like the simplist out of the remaining few.
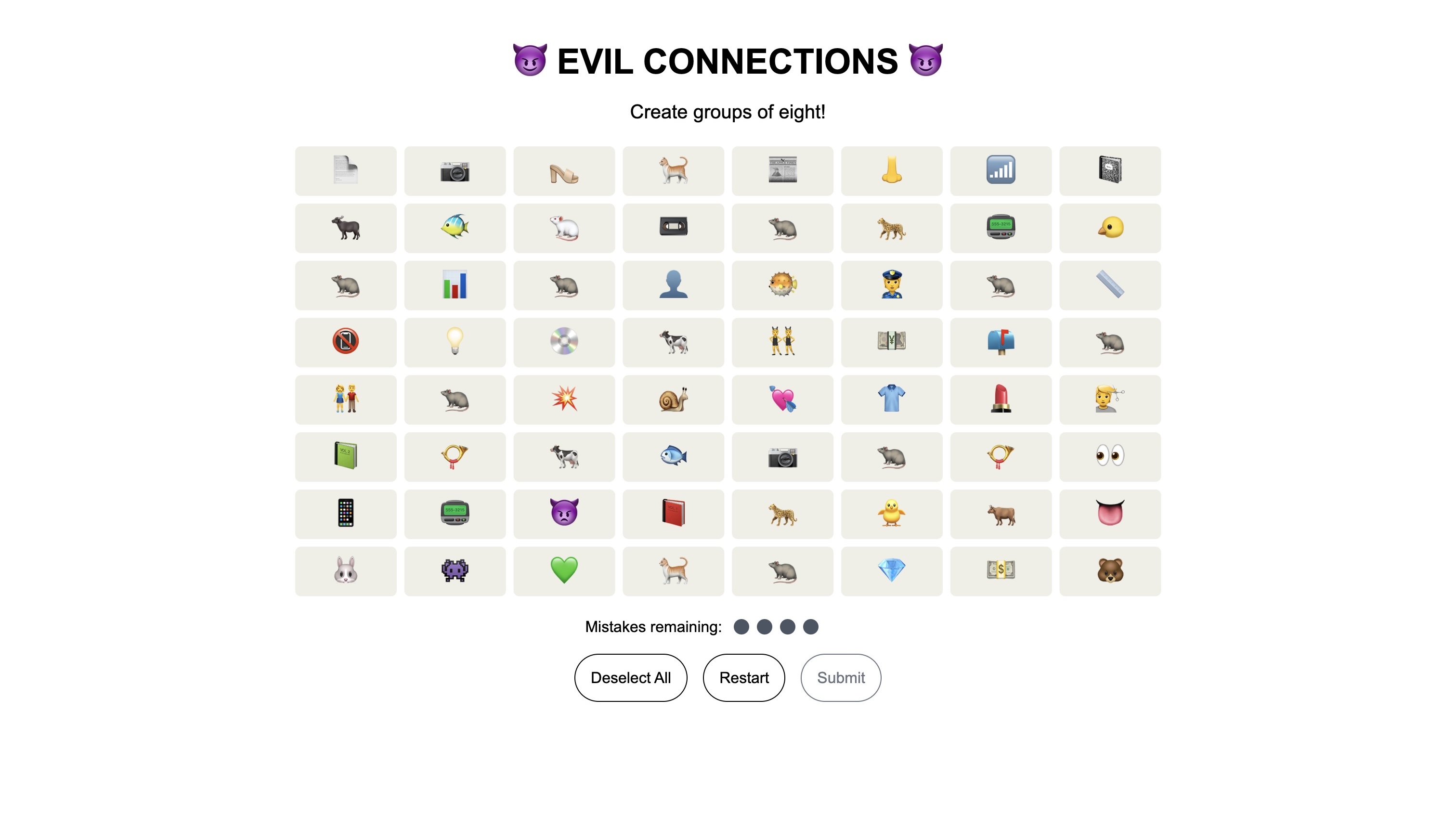
This puzzle started off with a lot of trial and error. It wasn’t just creating a group of eight emojis, but specific ones. As you clicked on different emojis, other cells would cycle through different emojis. The first group was easy since the rat never changed no matter what other cells you clicked.
I found group eight next with the evil emojis. This was helpful as it meant I didn’t have to go in order of groups.
I noticed that a set of emojis would always remain in certain cells. For example, the fish below would always remain in those cells. Other emojis outside like the dimaond or lipstick would never cycle into these cells. This meant that I could go through all the possible emojis within a cell to figure out a group.
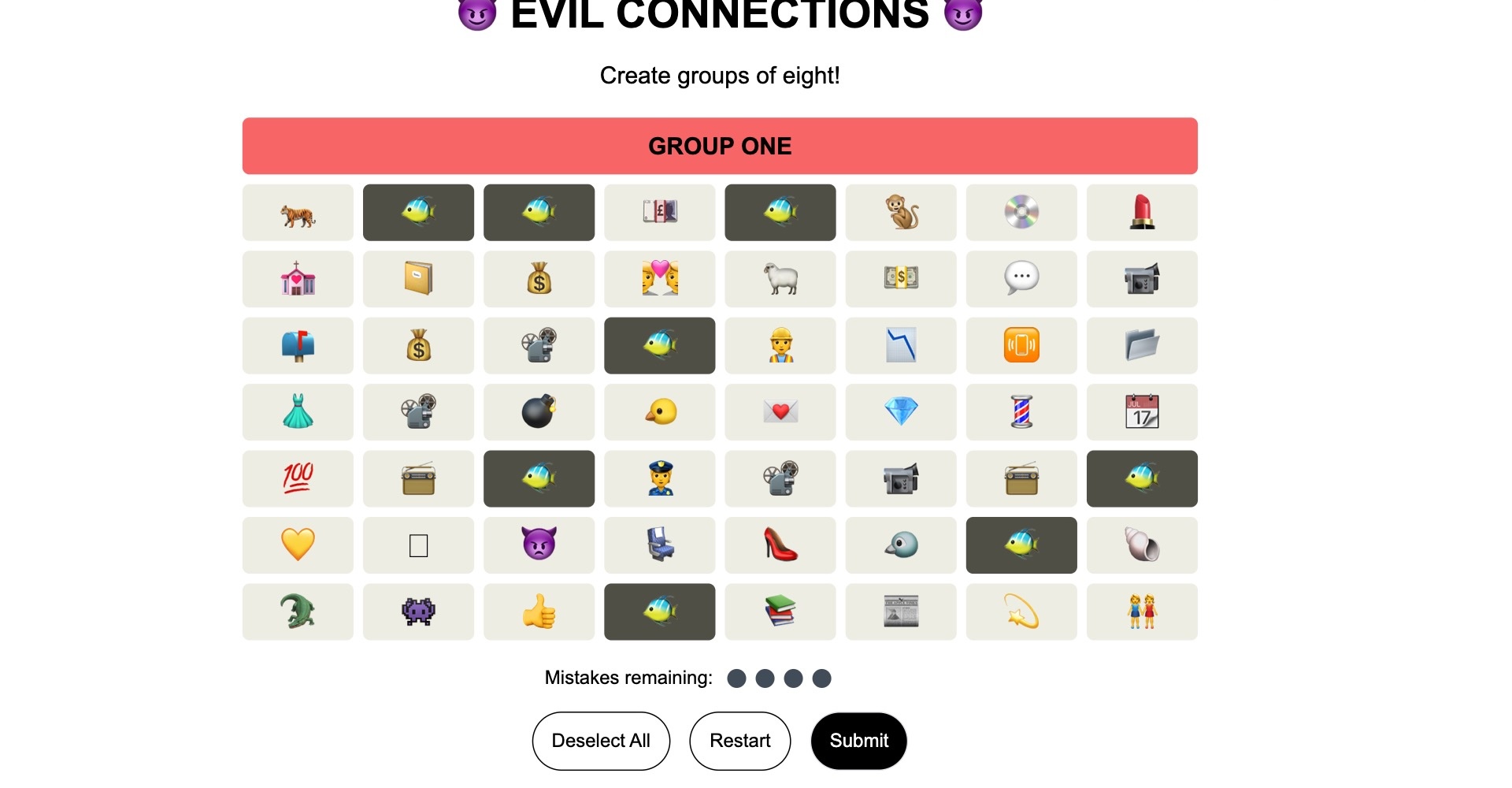
What’s frustrating is that at times the board would freeze and I’d be unable to continue with my run. I’d need to restart and try again from the start.
I figured out that group two was the white rat and group three was the ox. I theorized that groups were all animal related, so I tested those out first.
I discovered that certain cells would convert an emoji to another specific emoji. For example in the code block below, fish would convert to the white rat if you clicked cell F1 or A6 (letters being columns and numbers being rows). It would also work vice versa (F1/A6 converting white rat to fish).
Group 2
🐈🐠🐂🐄🐁🐐👀💀
B1,A2 🐂 -> 🐁
C1,A3 🐄 -> 🐁
D1,A4 🐈 -> 🐁
E1,A5 🐐 -> 🐁
F1,A6 🐠 -> 🐁
G1,A7 👀 -> 🐁
H1,A8 💀 -> 🐁
Using this mapping technique, I could convert all the emojis in group two to the white rat, then quickly swap to different emojis. This greatly sped up my testing. See below for my grid labelling.
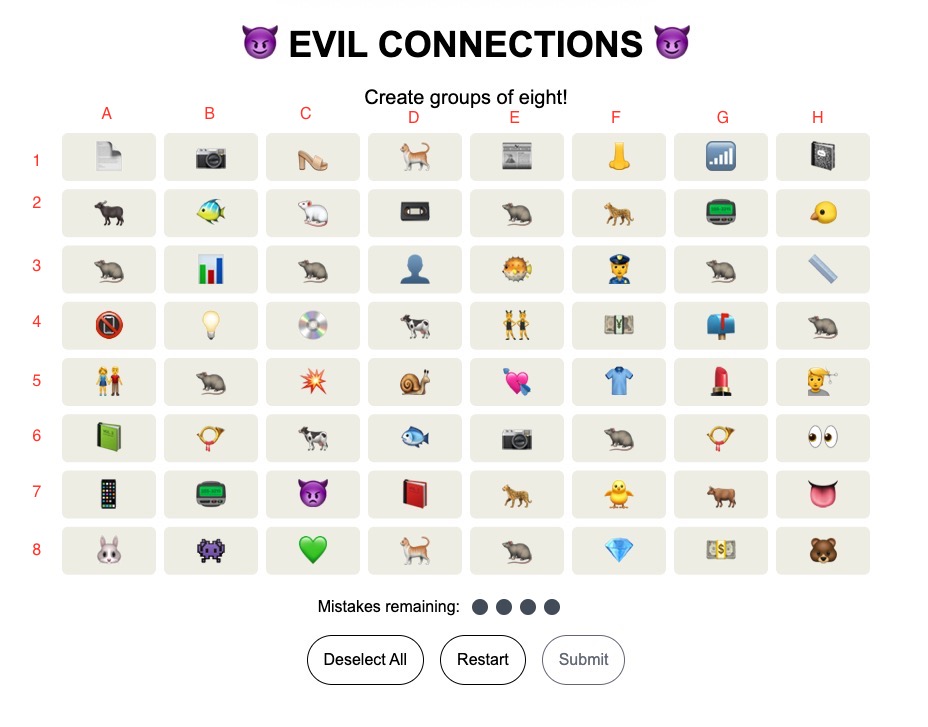
With this I slowly solved the rest in the following order: six, seven, five, and four.
After discovering all the groups, it was time to submit all of them. One problem with my mapping technique was that as you submitted groups, you’d lose a row and the remaining cells would be redistributed. It seemed to just shift the remaining cells down, so I started with the groups that had the most positions in the top row. For example, group four had three of it’s cells in the top row, so I started with it.
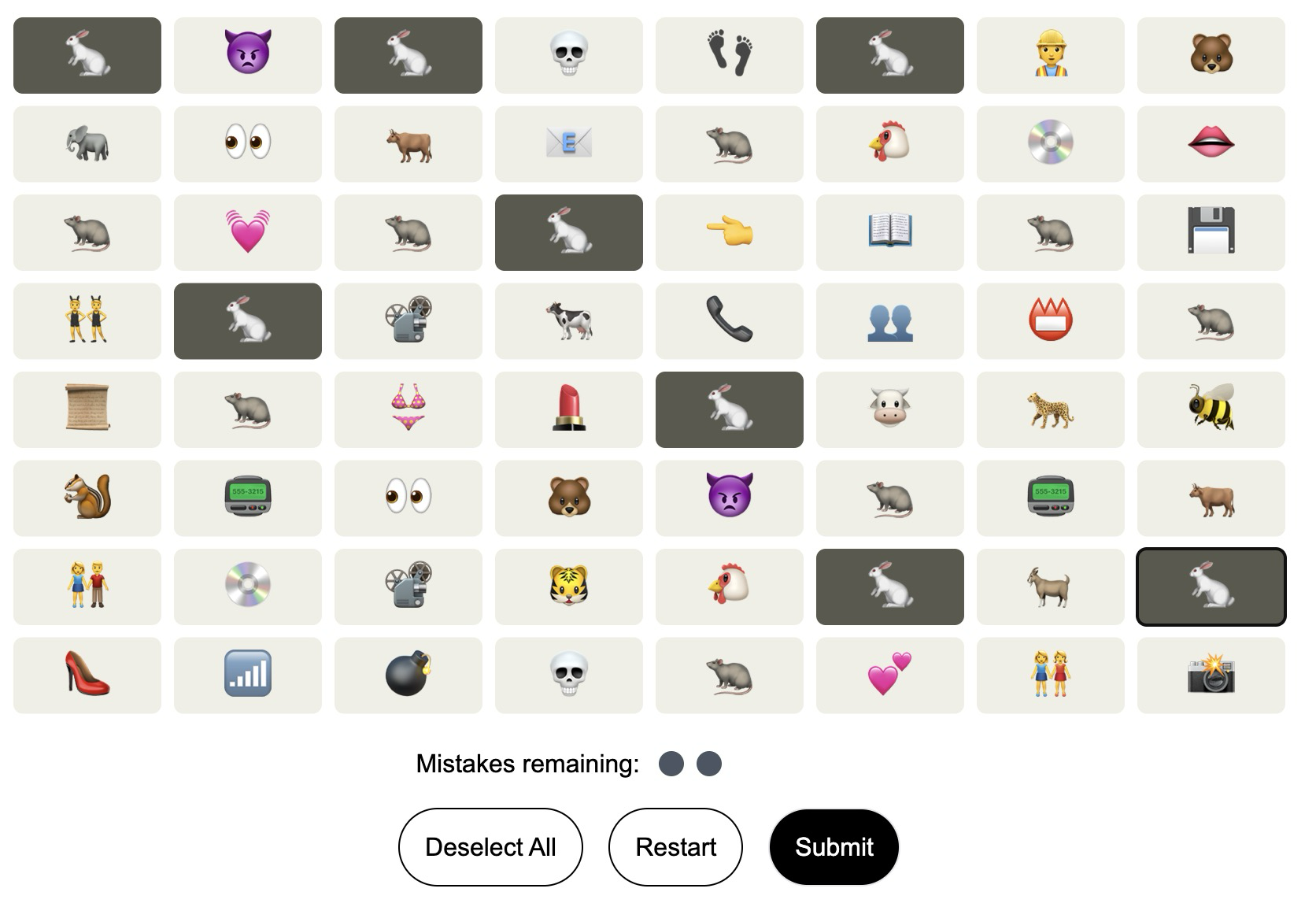
Eventually I’d reach a point where it was inevitable that I’d submit a group that screwed up the positions of anther group. I just cycled through the emojis to figure out where the cell was remapped, and continued.
The mapping technique greatly reduced my solve time, and I got it done in less than 20 minutes.
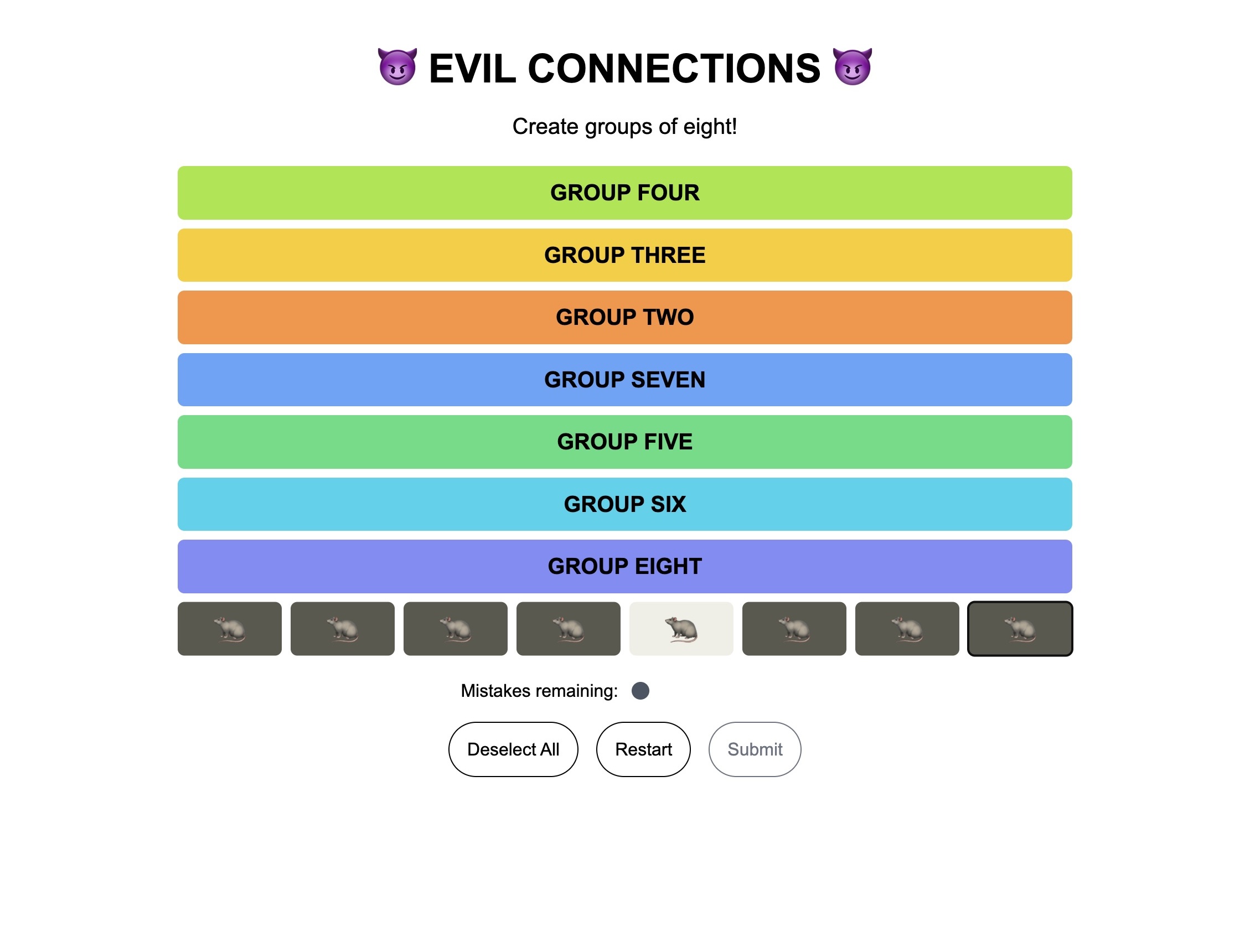
The mappings I used are on GitHub
Completed July 9, 2024.
Library (1000 points)
I was hesitant to do Library before Connections as I wasn’t sure if the 5 gusses at the bottom were refreshable or not. It was confirmed over the HackMIT Discord that it did refresh, so I did this one next.


For this one I decided to brute force the answer. I noted that the website sent a request to https://library.hackmit.org/api/puzzle/verify with the following payload:
{
"best": "45",
"worst": "46",
"uname": "jamesliangg_cb264c81"
}
Below is the response:
{
"flag": "incorrect",
"guesses_left": 4,
"verdict": {
"best": -2.4665,
"worst": 3.7023
}
}
It seemed to just submit the number of the book rather than the actual book title. This meant that I could just submit random numbers instead of the actual book titles. I created the following script (with a lot of help from GPT) to keep trying until it got the flag.
Completed July 9, 2024.
Hexhunt (2750 points)
Hexhunt was another puzzle I had no idea where to start.
Similar to Library, I decided to brute force this one. This website sent a request to https://hexhunt.hackmit.org/solve_hex_hunt with the following payload:
{
"letters": "AAAAAAAAAAAAAAAAAAA",
"userId": "jamesliangg_cb264c81"
}
Below is the response:
{
"top_word":"AA",
"total":2
}
I created a variety of scripts to create random strings and log the answers. Once I got an answer over 2k, I got a flag, but the score could be improved. I let the program run in the background while I doing other things.
Eventually I decided to use a script to try to improve existing high scores which brought my score higher.
Completed July 10, 2024. Stopped after July 25, 2024 due to no improvements after a week.
Wodou (1500 points)
Woudou was conceptually hard to understand. The boxes with Chinese characters would lead to random websites and they kept cycling through different possibilities. The answer key was confusing as unlike Wordle, there were five columns but six letters to fill.
Unlike Library or Hexhunt, I needed to get the Chinese characters before submission. The website sent a GET request to https://wodou.hackmit.org/api/generate?userEmail=jamesliangg_cb264c81 and got the following as a response:
{
"encodedWord": "近动交彶尾圾传宏扞再旬屼冴肓孙邨姒芳吕饭全怀劳扬灳朸圯如寿苍"
}
When submitting, it sent a request to https://wodou.hackmit.org/api/verify with a payload of:
{
"userEmail": "jamesliangg_cb264c81",
"encodedWord": "近动交彶尾圾传宏扞再旬屼冴肓孙邨姒芳吕饭全怀劳扬灳朸圯如寿苍",
"userInput": "abcdef"
}
Below is the response:
{
"feedback": [
"absent",
"absent",
"correct",
"present",
"present",
"absent"
],
"secretMessage": null
}
I decided to gather data before proceeding and sent a bunch of requests with random letters to log the data and results. They eventually added a rate limit to this, but luckily I had a lot of data to go through.
One of the links from the characters was a Wikipedia page on Chinese strokes. I theorized that there was a possible pattern since all the characters seemed pretty complex. I used https://www.chineseconverter.com/en/convert/chinese-stroke-order-tool to get the stroke count of characters manually and noted them down.
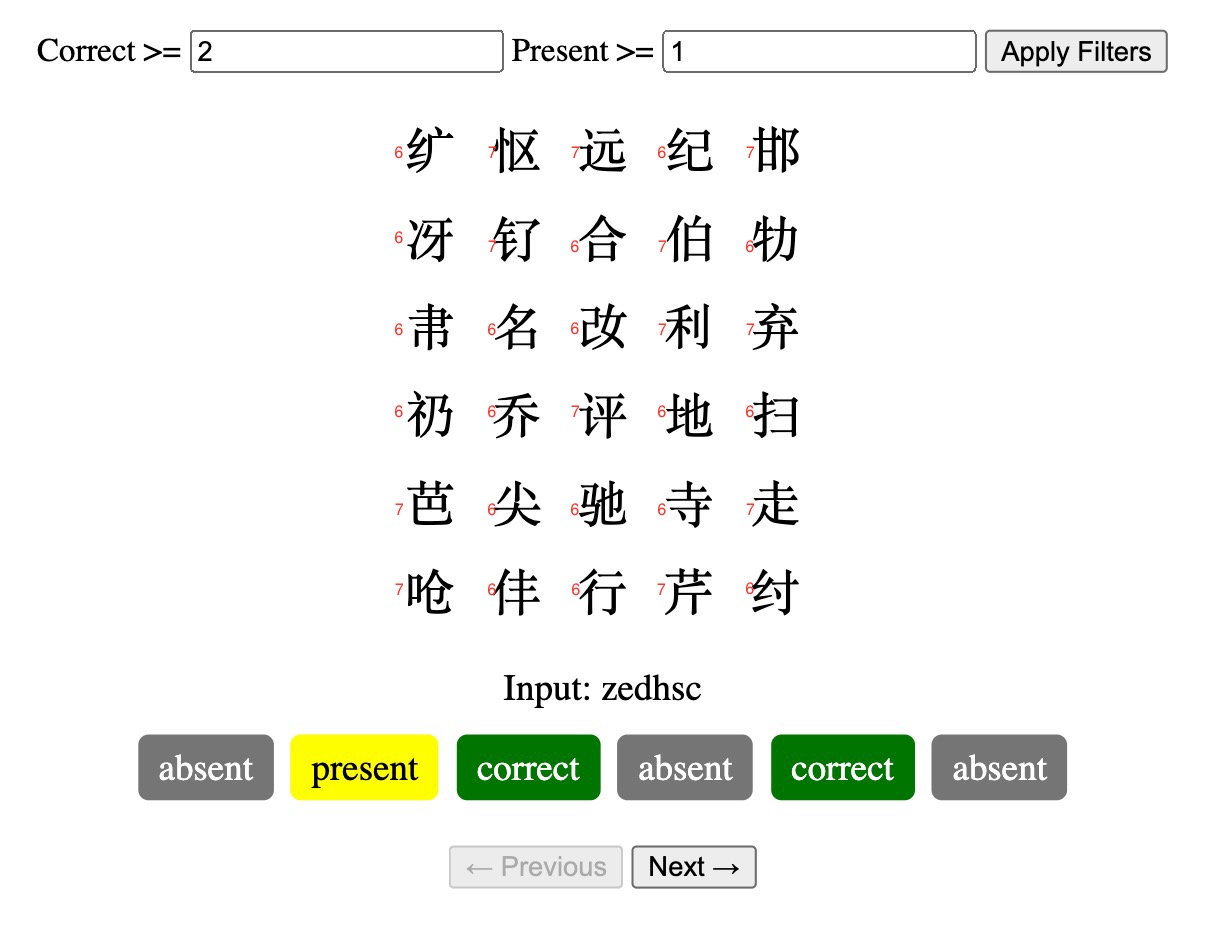
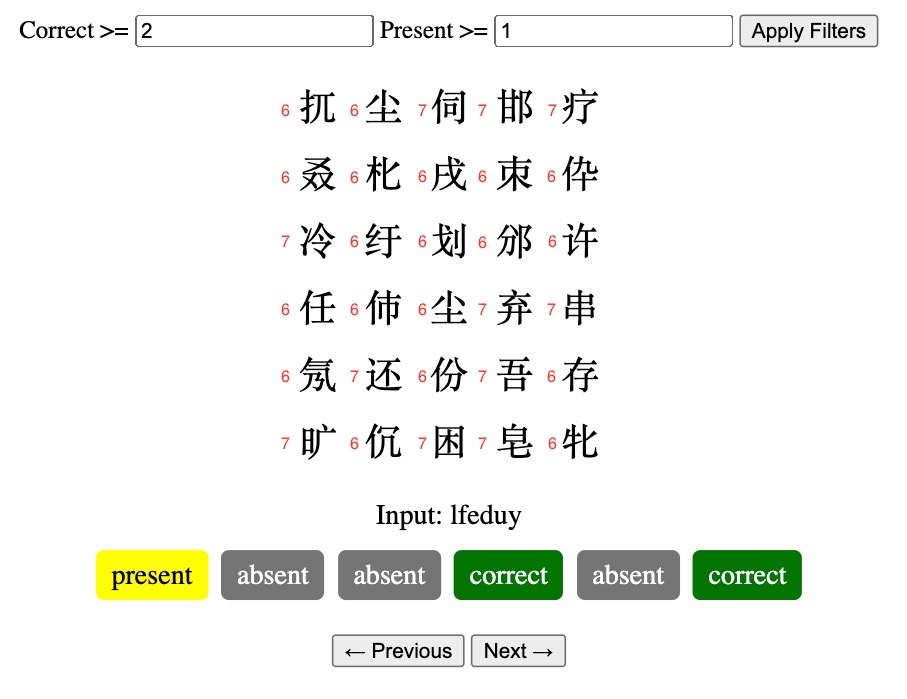
I noticed that it was always six or seven strokes. I scraped https://www.unicode.org/cgi-bin/GetUnihanData.pl?codepoint=%E5%9C%B6 to get the stroke count of characters (replace text after codepoint with character).
After sifting through the data I had earlier, I noticed that there was a pattern. I proceeded with the assumption that the first row mapped to the first letter, second row to second letter, etc. When the stroke order for row 5 was 6,6,7,6,6, the correct letter was always E. After verifying thise pattern with a few more letters, I created a script to search my data to get the correct letters based off the strokes of the input.

Completed July 13, 2024.
Twister (2250 points)
Similar to last year, I decided not to do this puzzle due to not understanding any explotation for binary.
Conclusion
In the end, I only solved 5/6 of the puzzles. I ended up finishing 58th on the leaderboard, falling out of top 50 on the very last day. If I continued on Hexhunt, I probably could’ve secured top 50, but I’m fine with landing in the top 20 during the first few days. Just like last year, it was a great experience and tons of fun.